Insider Threat
Early work on insiders addressed non-malicious but careless insiders; people who take risks to complete tasks efficiently as possible. We developed a common pool authentication method to create cooperative risk management that allows employees to optimize for their own tasks; and also requires that they do not create excess risk for the organization.
This was built upon the concept of a risk budget. Both the analytical economic optimization and human subjects experiments indicated that a risk-based budget approach will reduce risk by changing human decision-making.
The overall focus on malicious patterns, as opposed to malicious nodes, implements an assumption that the malicious insider is not intrinsically hostile. Extending this to a complex systems approach, we model malicious behaviors that emerge over time or in response to specific conditions.
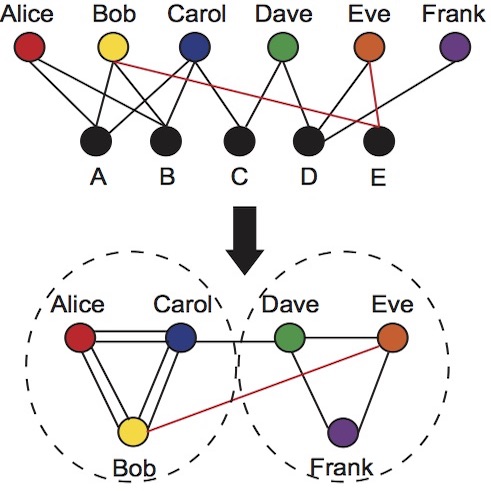
We modeled user-system interactions in a version control system as a temporal bipartite graph where interactions occur exclusively between two types of nodes, (i) users and (ii) software components. Note that the edges in this graph are only between these two types of nodes. A one-mode projection of this graph is the user graph in which two nodes (users) are connected if they have interacted at least once with the same component. Our methodology includes studying the evolution of the one-mode user graph to identify topological properties that characterize the system’s normal behavior. Among these observed properties, those that do not follow the norm of the regular pattern are assumed to indicate the presence of an anomalous event. Such an event may indicate a potential insider incident or, at least, an event that requires further investigation.
We modeled and compared the volume of interactions between users over similar or related components as opposed to non-related components over time. To capture sets of users with similar patterns of interaction, we relied on the notion of community structure to identify communities, or clusters, i.e., groups of nodes having higher probability of being connected to each other than to members of other groups. We showed that the volume of interactions between users that contribute to unrelated components increases when precipitating events are announced. This indicates the impact of precipitating events in increasing the likelihood of a change in the interacting behavior between users and components, and hints at the scale of undetected insider information exfiltration.
Publications
| Articles in journals or book chapters (5) |
-
Pablo Moriano,
Jared Pendleton,
Steven Rich,
and L. Jean Camp.
Stopping the Insider at the Gates: Protecting Organizational Assets Through Graph Mining.
Journal of Wireless Mobile Networks, Ubiquitous Computing, and Dependable Applications,
9(1):4--29,
2018.

Keywords: Insider Threat. [bibtex-entry] -
Debin Liu,
Ninghui Li,
XiaoFeng Wang,
and L. Jean Camp.
Beyond Risk-Based Access Control: Towards Incentive-Based Access Control.
Financial Cryptography and Data Security,
pp 102--112,
2012.
Note: Springer Berlin/Heidelberg.
Keywords: Insider Threat. [bibtex-entry] -
Debin Liu,
Ninghui Li,
XiaoFeng Wang,
and L. Jean Camp.
Security Risk Management using Incentives.
IEEE Security and Privacy,
2011.
Note: IEEE Computer Society.
Keywords: Economics of Security, Insider Threat. [bibtex-entry] -
Debin Liu,
L. Jean Camp,
XiaoFeng Wang,
and Lusha Wang.
Using Budget-Based Access Control to Manage Operational Risks Caused by Insiders.
Journal of Wireless Mobile Networks, Ubiquitous Computing, and Dependable Applications,
1(1):29--45,
2010.

Keywords: Economics of Security, Insider Threat. [bibtex-entry] -
Debin Liu,
XiaoFeng Wang,
and L. Jean Camp.
Game-theoretic modeling and analysis of insider threats.
International Journal of Critical Infrastructure Protection,
1:75--80,
2008.
Note: Elsevier.
Keywords: Economics of Security, Insider Threat. [bibtex-entry]
| Conference publications (2) |
-
Pablo Moriano,
Jared Pendleton,
Steven Rich,
and L. Jean Camp.
Insider Threat Event Detection in User-System Interactions.
In 9th ACM CCS International Workshop on Managing Insider Security Threats (MIST),
Dallas, TX, USA,
pages 1--12,
2017.
Keywords: Insider Threat. [bibtex-entry] -
L. Jean Camp.
Hardening the Network from the Friend Within.
In Information Security and Privacy,
pages 249--249,
2009.
Springer.
Keywords: Insider Threat. [bibtex-entry]