SDN
 What are the challenges, threats, implications and potential for SDN in terms of creating a resilient network? To answer this question, we have created clear threat models grounded in documented and realistic use cases; extracted resulting enumerated authentication requirements; implemented one case of the necessary next-generation network modeling to evaluate authentication interactions, such that the models address all layers from physical to human; and finally the demonstrated practical forward movement to meeting these challenges as an open source network component named Bongo.
What are the challenges, threats, implications and potential for SDN in terms of creating a resilient network? To answer this question, we have created clear threat models grounded in documented and realistic use cases; extracted resulting enumerated authentication requirements; implemented one case of the necessary next-generation network modeling to evaluate authentication interactions, such that the models address all layers from physical to human; and finally the demonstrated practical forward movement to meeting these challenges as an open source network component named Bongo.
Many of the vulnerabilities in the current Internet, especially those associated with BGP, can be attributed to the complexity of network management in the existing IP networks. Currently network management requires distributed management and manual configurations of individual devices, often using low level commands or scripts. The current coexistence of the control and data planes on the same network amplifies such vulnerabilities. For instance, the misconfigurations of BGP results in routing failures, as in the myriad examples offered below. The combination of data and control causes an invisibility of physical risks and choke points. Conversely, the necessary openness for configuration of individual devices results in high levels of network device information availability for attackers.
Software Defined Networking isolates the control and data planes. This separation enables a level of abstraction that can resolve many current network vulnerabilities. SDN has the potential to resolve longstanding challenges in authentication in routing and traffic management (mitigating outages and denial of service). In traditional security terms, SDN can address authentication, integrity, and availability. The move to SDN presents an extremely rare point of inflection which offers the potential to leverage the economics of SDN to harden the network as a whole. The demonstration implemented under this contract proves SDN can be secured, and when secured in an incentive-aware manner, simultaneously improves reliance in the BGP network to which it connects.
Yet there is a risk SDN will be adopted in an insecure manner, repeating and exacerbating the vulnerabilities of today's network. Investment in security lags; for example, only one SDN switch supports even basic TLS. Issues of security network management applications, evaluation of complex interactions, and the inseparable economic and usability questions are unexplored. This report enumerates both the potential of SDN and the challenges in meeting that potential. As noted, the associated research project illustrates substantive proof of progress in terms of securing SDN and leveraging SDN to increase BGP reliance, as well as moving forward network modeling to identify emergent concerns before these become practical problems. More specifically, this report described the path and achievements under FA8750-13-2-0023. The initial approach to resilient SDN was domain-specific.
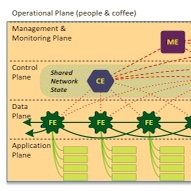
In order to create a comprehensive view of future attacks and thus emergent security requirements, we began the project with a set of critical use cases. As the critical use cases matured, the threat model reified, and the project moved directly to a vision of the security challenges as existing at distinct layers rather than being differentiated by domain. The result is a comprehensive description of both the threat models and the authentication requirements for reliable network management. A critical part of this threat model is the recognition of the need for a management plane to leverage all the potential of SDN for simultaneous simplification of network management and assurance of network reliance. Thus we identify threats on a data plane (isolated from but informing the control plane), the control plane, the management plane, and the human layer where final decision-making authority resides.
In addition to identifying threats from data to human layers, our initial modeled characterized the unique properties of SDN via network modeling. SDN network components are fundamentally different from the model where the routing decisions, the data flow, and the routing table are all contained in a single channel passing through a physical box, one physical component. In contrast, many virtual switches and the 3 associated controller may exist on a single machine, or tens of switches may exist on one machine isolated from the controller. In addition to the physical complexity, each type of component must be defined as having very different types across and within layers. One component of the report is provable case of complex modeling using constructs from other disciplines, thus enabling us to address isolation, reachability, and the possibility of cascading failures. The ultimate outcome of such modeling is informing authentication and thus management requirements to create a network that enables individual entities to be immune to certain classes of attacks, and identify situations in which limited diffusion of a defense can enable network-wide immunity.
To show that progress in the immense multi-disciplinary challenge comprised by these threats and the requirements on these solutions we constructed a proof-of-concept. This proof of concept (named 'Bongo' to align with the equine theme of Zebra, Quagga, etc) translates a series of route updates into a RIB, which is then converted to a flow information base (FLIB). The FLIB then can be subject to arbitrary analysis to identify different types of attacks. In particular, content-leaking misdirection attacks via incorrect routing announcements becomes immediately identifiable.
Publications
| Articles in journals or book chapters (1) |
-
Kevin Benton,
L. Jean Camp,
Tim Kelley,
and Martin Swany.
Filtering Source-Spoofed IP Traffic Using Feasible Path Reverse Path Forwarding with SDN.
International Journal of Computer and Communication Engineering,
5(6):441,
2016.

Keywords: SDN. [bibtex-entry]
| Conference publications (1) |
-
Kevin Benton,
L. Jean Camp,
Tim Kelley,
and Martin Swany.
Filtering IP source spoofing using feasible path reverse path forwarding with SDN.
In Communications and Network Security (CNS), 2015 IEEE Conference on,
pages 733--734,
September 2015.
IEEE.

Keywords: Network Engineering, SDN. [bibtex-entry]
